In this Tutorial I will configure Secure Firewall Threat Defense (originally – Firepower Threat Defense) (FTD) High Availability setup (Active/Standby failover) with one existing FTD Appliance (ftd1) and one new FTD Appliance (ftd2).
This process is commonly used if there is already one Firewall Threat Defense in production environment and the second Firewall Threat Defense must be added because of the high-availability needs into the HA Active/Standby “cluster” without changing network Gateway IP configuration on all devices in the network.
Both Firewall Threat Defense Appliances must meet following conditions:
- Same model.
- Same version- this applies to FXOS and to FTD – major (first number), minor (second number), and maintenance (third number) must be equal.
- Same number of interfaces.
- Same type of interfaces.
- Both devices as part of the same group/domain in FMC.
- Have identical Network Time Protocol (NTP) configuration.
- Be fully deployed on the FMC without uncommitted changes.
- Be in the same firewall mode: routed or transparent.
Source:
Before the start of the configuration it is recommended to create backups of the FTD Appliance and Firewall Management Center (FMC).
Prerequisites:
- running Cisco Secure Firewall Management Center
- running Cisco Secure Firewall Threat Defense (FTD) already connected with Firewall Management Center
- new Firewall Threat Defense (FTD) already registered with Firewall Management Center (FMC)
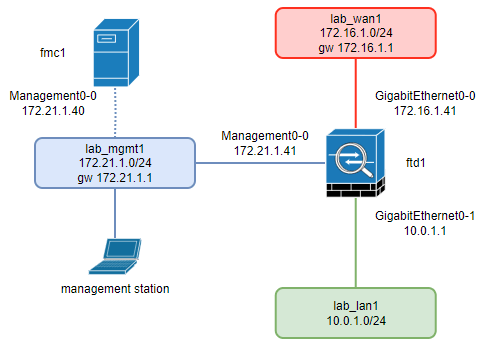
1. Initial and Target Situation
Initial Situation:
FTD Appliance:
External Interface:
Default gateway:
Internal Interface:
ftd1
Gi0-0 172.16.1.41/24
172.16.1.254
Gi0-1 1 10.0.1.1/24
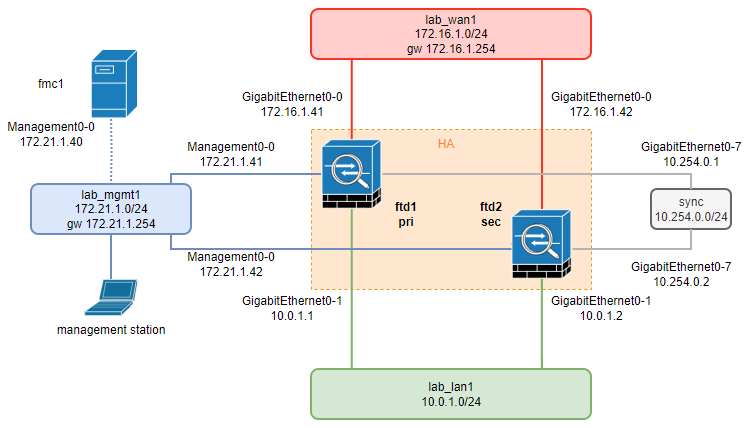
Target Situation:
FTD Appliance:
External Interface:
Default gateway:
Internal Interface:
Sync Interface:
ftd1
Gi0-0 172.16.1.41/24
172.16.1.254
Gi0-1 1 10.0.1.1/24
Gi0-7 10.254.0.1/24
ftd2
Gi0-0 172.16.1.42/24
172.16.1.254
Gi0-1 1 10.0.1.2/24
Gi0-7 10.254.0.2/24
Initial Situation Diagram:
Target Situation Diagram:
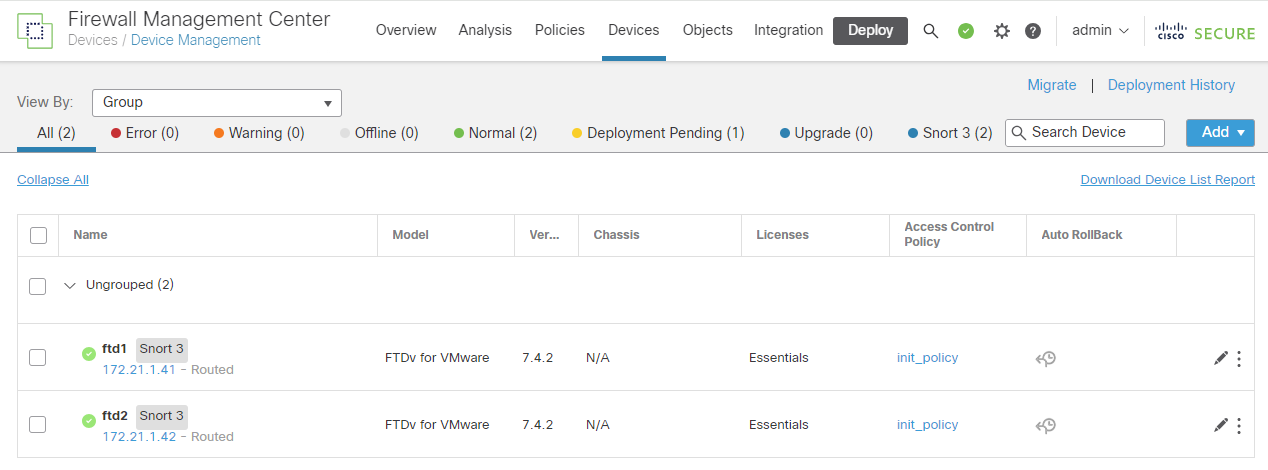
Initial FMC Status:
2. Configure FTD High Availability
2.1 TIP: On the existing FTD Appliance Configure Active/Standby MAC Address for all Data Interfaces
The Firewall Threat Defense device does not send gratuitous ARPs for static NAT addresses when the MAC address changes, so connected routers do not learn of the MAC address change for these addresses. Virtual MAC addresses guard against this disruption, because the active MAC addresses are known to the secondary unit at startup, and remain the same in the case of new primary unit hardware. If you do not configure virtual MAC addresses, you might need to clear the ARP tables on connected routers to restore traffic flow.
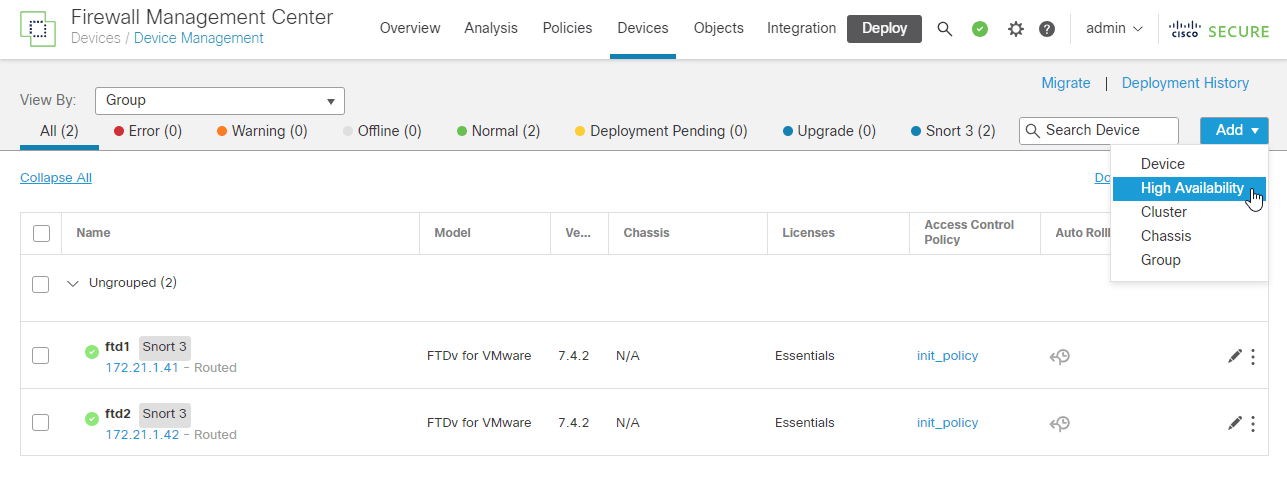
2.2 add High Availability
Devices > Device Management > Add > High Availability
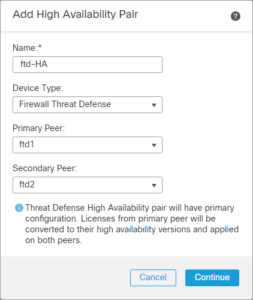
2.3 Add High Availability Pair
Name: ftd-HA
Device Type: Firewall Threat Defense
Primary Peer: ftd1
Secondary Peer: ftd2
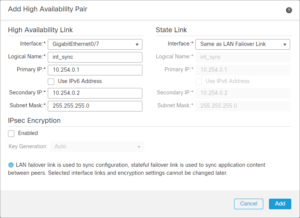
2.4 Add High Availability Pair – High Availability Link
Interface: GigabitEthernet0/7
Logical Name: int_sync
Primary IP: 10.254.0.1
Secondary IP: 10.254.0.2
Subnet Mask: 255.255.255.0
IPsec Encryption: (according to your needs)
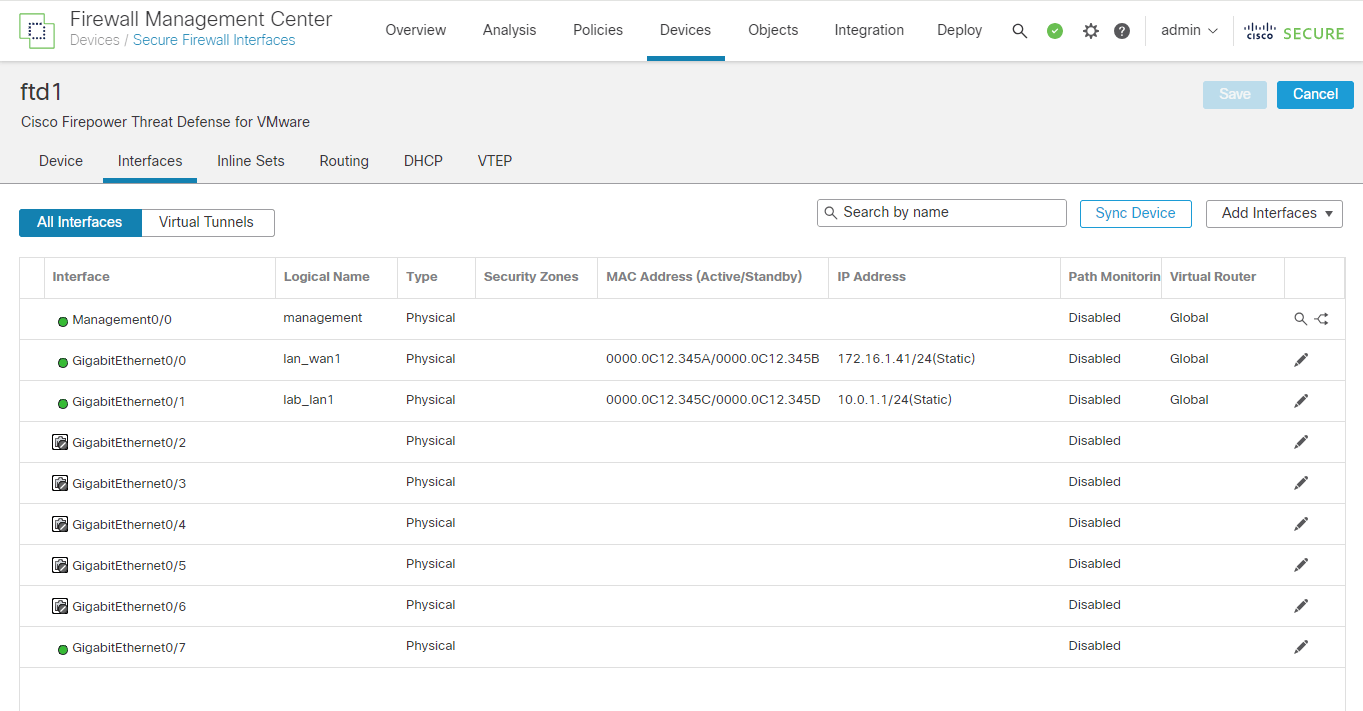
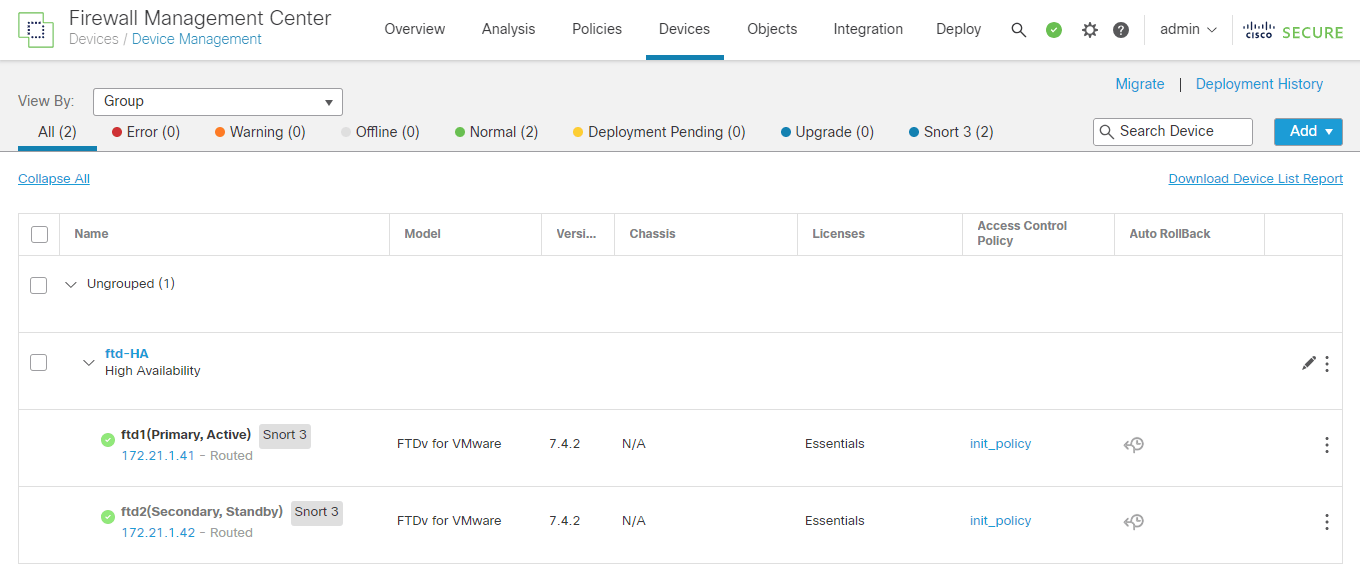
2.5 Device Status (after couple of minutes)
3. Conclusion
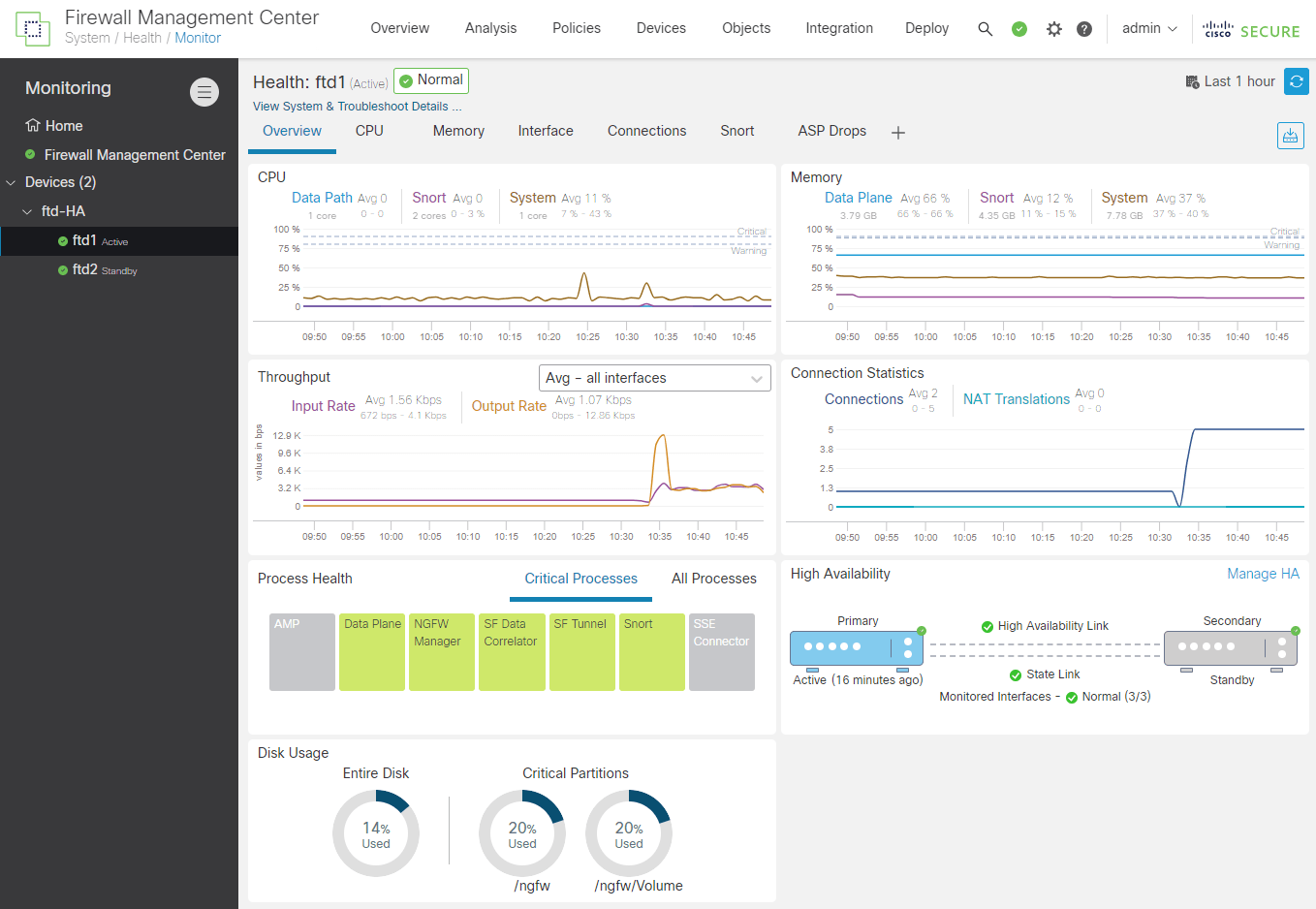
The new Firewall Threat Defense HA Pair is up and running at normal conditions.