In this article I will describe Check Point Remote Access – Secure Configuration Verification and demonstrate how to implement it with the Check Point Mobile for Windows.
Use Case
- Network and Firewall administrators can use different tools to control computers inside their organization. For example, to disable dangerous components such as Java and ActiveX controls in browsers, install Anti-Virus, and make sure they are run correctly.
- For remote users who access the organization from outside of the LAN, the administrator cannot enforce control of the computer with the same tools. For example, suppose the remote user has ActiveX enabled, and connects to a website containing a malicious ActiveX control which infects his or her computer. When the remote user connects to the organization’s LAN, the LAN becomes vulnerable as well.
- A properly configured Desktop Security Policy, cannot protect against this type of attack, because the attack does not target a vulnerability in the access control to the endpoint computer. Instead it takes advantage of the vulnerable configuration of applications on the endpoint computer.
Source:
R81 Remote Access VPN Administration Guide – Use Case
Introduction to Secure Configuration Verification (SCV)
Secure Configuration Verification (SCV) makes sure that remote access client computers are configured in accordance with the enterprise Security Policy. Use SCV to:
- Get reports on the configuration of remote clients.
- Make sure that clients comply with the organization’s security policy.
- Block connectivity from clients that do not comply.
SCV does not replace the Desktop Security Policy, but works with it.
SCV uses SCV checks, which are DLLs (plug-ins) on the client, that are invoked and enforced according to the policy that you configure on the Management Server. SCV checks include sets of conditions that define a securely configured client system. Checks can include, for example, the user’s browser configuration, the version of the Anti-Virus software installed on the desktop computer, and the operation of the personal firewall policy. These security checks are performed at pre-defined intervals by the remote access client. Based on the results of the SCV checks, the Security Gateway decides whether to allow or block connections from the client to the LAN.
- If the client passes all of the SCV checks, the client is compliant. The Security Gateway allows the connection.
- If the client fails one of the SCV checks, it is not compliant. You can configure the Security Gateway to reject connections from non-compliant endpoint computers, or to accept such connections and create a log entry.
Check Point’s SCV solution comes with many predefined SCV checks for the operating system and user’s browser, and also allows OPSEC partners, such as Anti-Virus software manufacturers, to add SCV checks for their own products.
Source:
R81 Remote Access VPN Administration Guide – Introduction to SCV
Prerequisites:
- running Security Management Server
- running Checkpoint Security Gateway already connected with Security Management Server
- running Windows System with installed Check Point Mobile for Windows
1. Enable Secure Configuration Verification on Security Management Server
2. Enable Policy Server on Security Gateway
3. Configure Security Policy for Desktop Security
4. Configure Compliance Rules for Client
5. Configure Security Policy Rules
6. Install Check Point Mobile for Windows
7. Configure Site in Check Point Mobile
1. Enable Secure Configuration Verification on Security Management Server
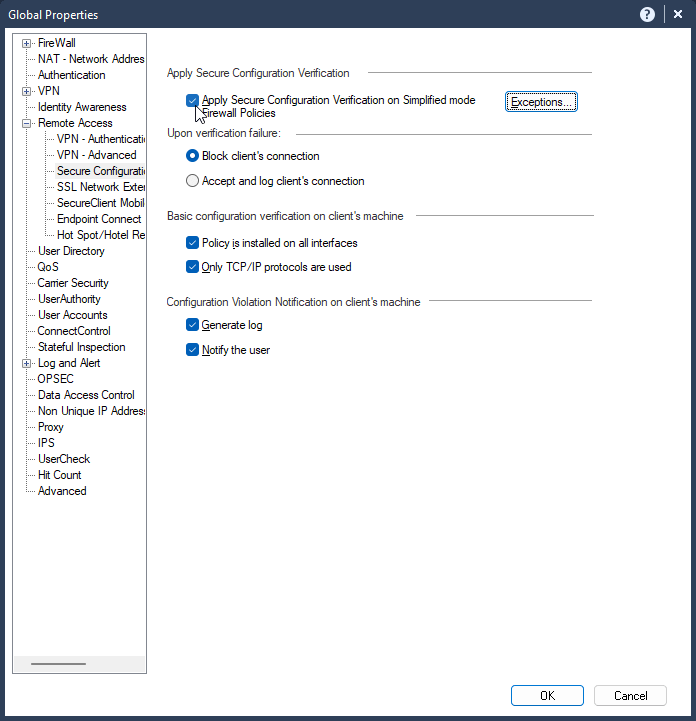
1.1 Enable in Menu / Global Properties / Remote Access / Secure Configuration Apply Secure Configuration Verification (SCV) / Apply Secure Configuration Verification on Simplified mode Firewall Policies
1.2 Install Database
2. Enable Policy Server on Security Gateway
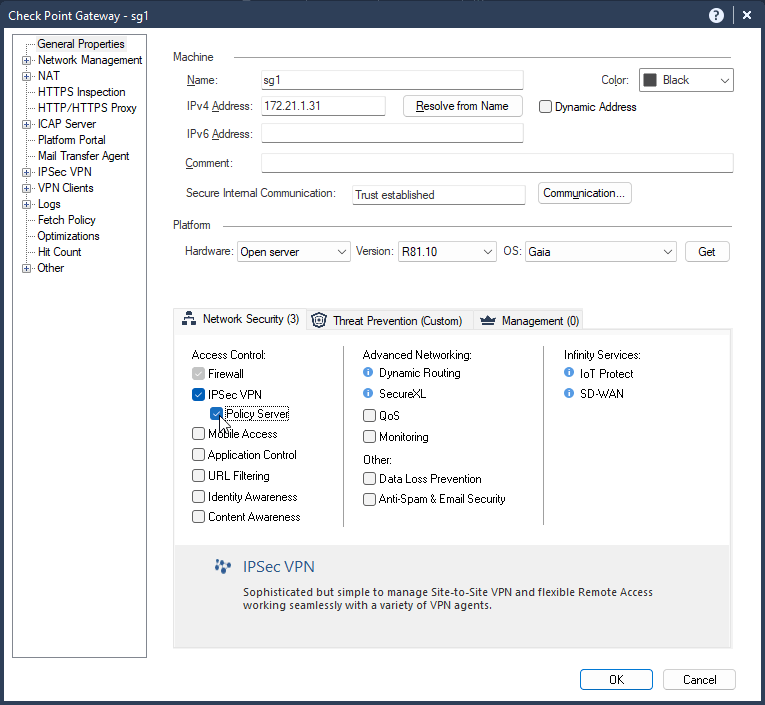
2.1 Enable in Gateway Object / General Properties / IPSec VPN / Policy Server
3. Configure Security Policy for Desktop Security
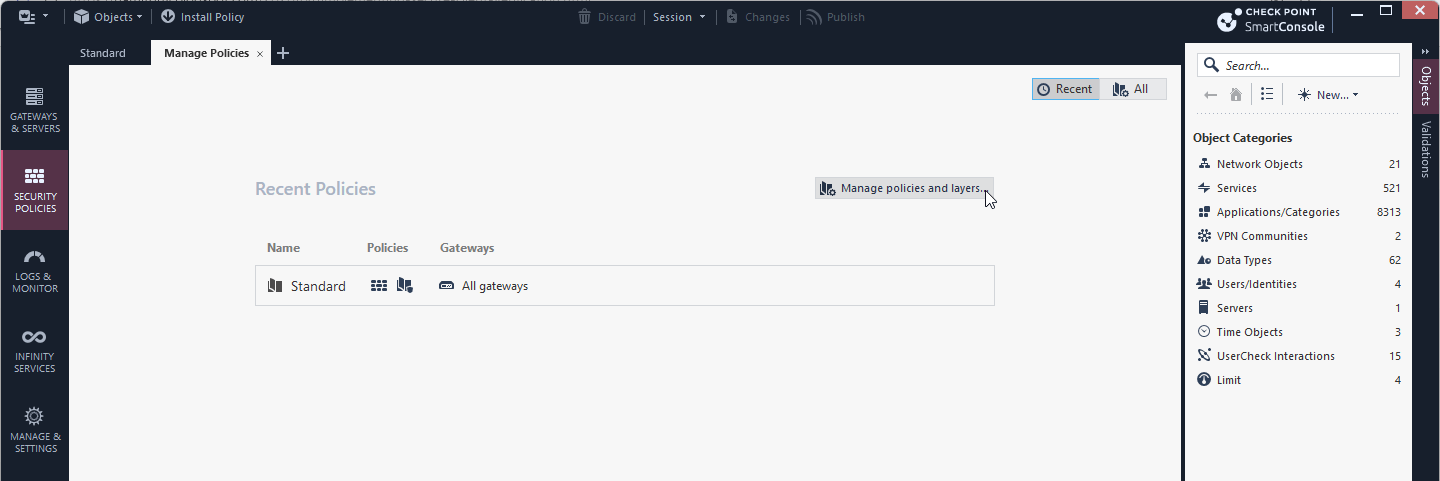
3.1 Security Policies / Manage Policies / Manage policies and layers
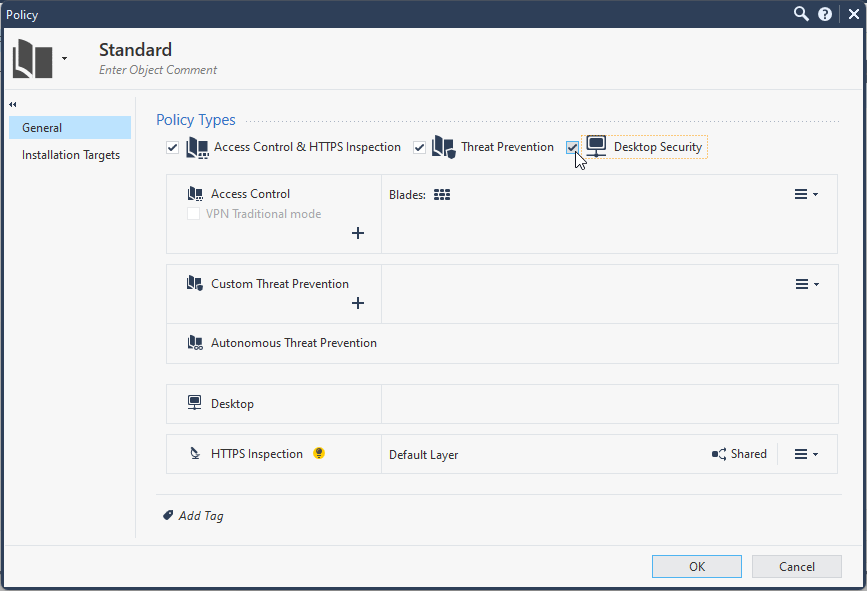
3.2 Edit Policy “Standard“
3.3 Enable Desktop Security Policy Type
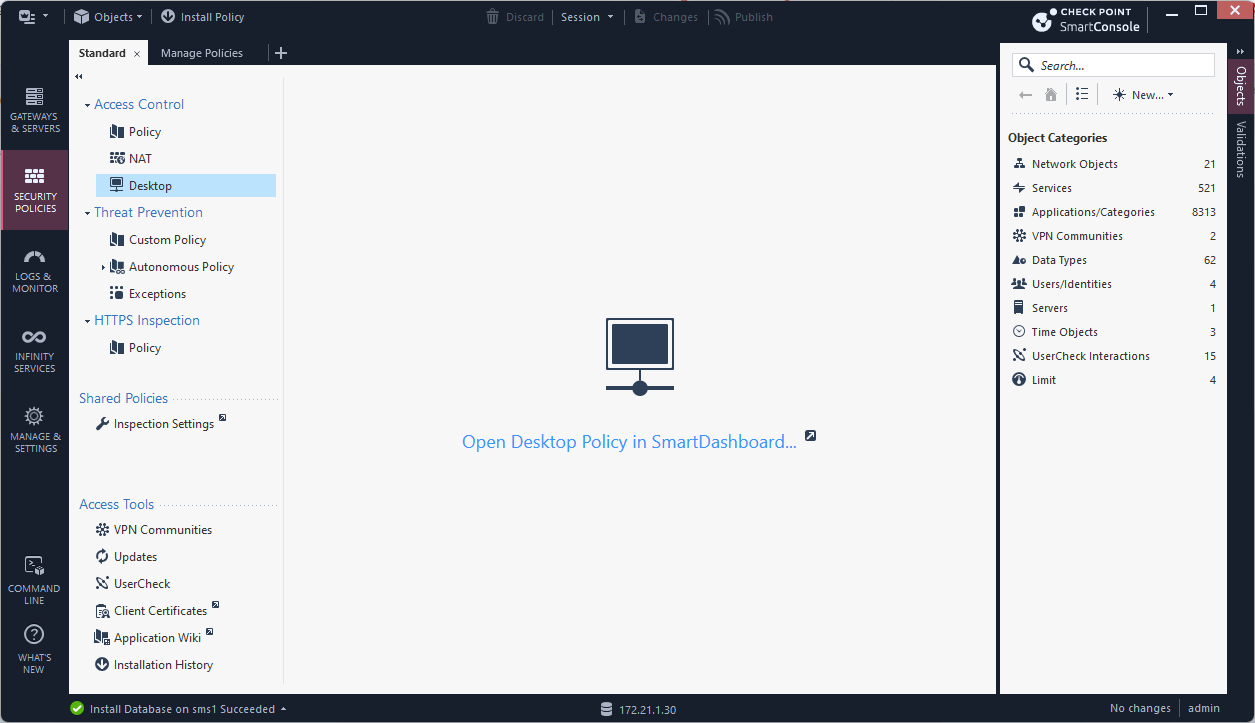
3.4 Security Policies / Standard / Desktop / Open Desktop Policy in SmartDashboard
Note:
- Secure Verification Configuration File will be only deployed when there is at least one rule in the desktop policy present
- with the Check Point Mobile for Windows this rule will not be enforced on the Client (because Check Point Mobile for Windows does not have local Firewall feature)
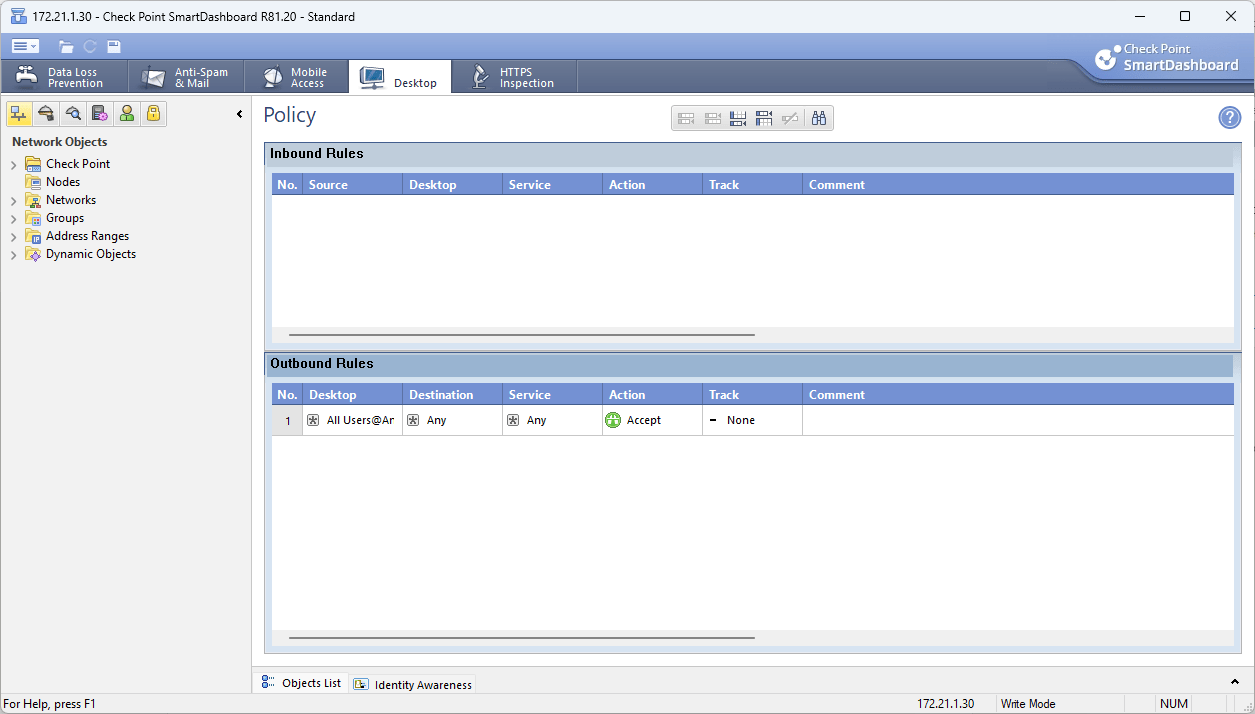
3.5 Add Rule e.g. – Outbound Rules / Add Rule at the Bottom
3.6 SmartDashboard / Menu / Update
4. Configure Compliance Rules for Client
- Compliance Rules are stored on the Security Management Server in file $FWDIR/conf/local.scv
- This file is deployed from Security Management Server to the Security Gateway every policy install
- RAS Client downloads this file after successful RAS VPN authentication from the Gateway and runs the Compliance checks
Link – Check Point Introduction to the local.scv file
In my example I will make following compliance checks:
- OsMonitor plugin
- screen saver minutes 3 min
- screen saver password protected
- Windows 11
- major_os_version_number_11 (10)
- ProcessMonitor plugin
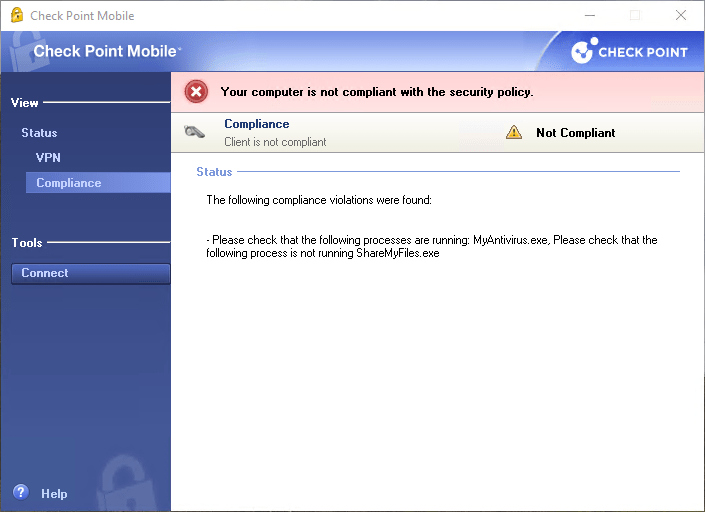
- if process “MyAntivirus.exe” is running
- if process “ShareMyFiles.exe” is not running
- RegMonitor plugin
- if the compluter is registered in domain testdomain.com
Under the Section – Global Parameters:
- if client is not compliant – block connections and disconnect from VPN
- :disconnect_when_not_verified (true)
- :block_connections_on_unverified (true)
- Check Point Mobile Client for Windows has not Firewall feature included therefore :skip_firewall_enforcement_check (true) must be set to true
There are Plenty of other fully customizable Compliance Check conditions in local.scv, e.g.:
- Browser Monitor – minor/minor versions, run ActiveX allowed
- OsMonitor -minor/major OS Version, minor/major Service Pack Version
- ProcessMonitor – is/is not running
- groupmonitor – logged in user is member of the AD Group
- HotFixMonitor – is hotfix abc installed
- AntiVirusMonitor – antivirus signature >= n
- ScriptRun – .bat script for verification
- RegMonitor – verify Registry Key values
- SCVMonitor – SCV package version verification
- sc_ver_scv – parameters for Check Point Secure Client
My Sample local.scv file:
(SCVObject
:SCVNames (
: (user_policy_scv
:type (plugin)
:parameters (
)
)
: (BrowserMonitor
:type (plugin)
:parameters (
:browser_major_version (5)
:browser_minor_version (0)
:browser_version_operand (">=")
:browser_version_mismatchmassage ("Please upgrade your Internet browser.")
:intranet_download_signed_activex (disable)
:intranet_run_activex (disable)
:intranet_download_files (disable)
:intranet_java_permissions (disable)
:trusted_download_signed_activex (disable)
:trusted_run_activex (disable)
:trusted_download_files (disable)
:trusted_java_permissions (disable)
:internet_download_signed_activex (disable)
:internet_run_activex (disable)
:internet_download_files (disable)
:internet_java_permissions (disable)
:restricted_download_signed_activex (disable)
:restricted_run_activex (disable)
:restricted_download_files (disable)
:restricted_java_permissions (disable)
:send_log (alert)
:internet_options_mismatch_message ("Your Internet browser settings do not meet policy requirements\nPlease check the following settings:\n1. In your browser, go to Tools -> Internet Options -> Security.\n2. For each Web content zone, select custom level and disable the following items: DownLoad signed ActiveX, Run ActiveX Controls, Download Files and Java Permissions.")
)
)
: (OsMonitor
:type (plugin)
:parameters (
:os_version_mismatchmessage ("Please upgrade your operating system.")
:enforce_screen_saver_minutes_to_activate (3)
:screen_saver_mismatchmessage ("Your screen saver settings do not meet policy requirements\nPlease check the following settings:\n1. Right click on your desktop and select properties.\n2. Select the Screen Saver tab.\n3. Under Wait choose 3 minutes and check the Password Protection box.")
:send_log (alert)
:major_os_version_number_2k (5)
:minor_os_version_number_2k (0)
:os_version_operand_2k ("==")
:service_pack_major_version_number_2k (0)
:service_pack_minor_version_number_2k (0)
:service_pack_version_operand_2k (">=")
:major_os_version_number_xp (5)
:minor_os_version_number_xp (1)
:os_version_operand_xp ("==")
:service_pack_major_version_number_xp (0)
:service_pack_minor_version_number_xp (0)
:service_pack_version_operand_xp (">=")
:major_os_version_number_2003 (5)
:minor_os_version_number_2003 (2)
:os_version_operand_2003 ("==")
:service_pack_major_version_number_2003 (0)
:service_pack_minor_version_number_2003 (0)
:service_pack_version_operand_2003 (">=")
:major_os_version_number_7 (6)
:minor_os_version_number_7 (1)
:os_version_operand_7 ("==")
:service_pack_major_version_number_7 (0)
:service_pack_minor_version_number_7 (0)
:service_pack_version_operand_2003 (">=")
:major_os_version_number_8 (6)
:minor_os_version_number_8 (2)
:os_version_operand_8 ("==")
:service_pack_major_version_number_8 (0)
:service_pack_minor_version_number_8 (0)
:service_pack_version_operand_8 (">=")
:major_os_version_number_81 (6)
:minor_os_version_number_81 (3)
:os_version_operand_8 ("==")
:service_pack_major_version_number_81 (0)
:service_pack_minor_version_number_81 (0)
:service_pack_version_operand_81 (">=")
:major_os_version_number_10 (10)
:minor_os_version_number_10 (0)
:os_version_operand_10 ("==")
:service_pack_major_version_number_10 (0)
:service_pack_minor_version_number_10 (0)
:service_pack_version_operand_10 (">=")
:major_os_version_number_11 (10)
:minor_os_version_number_11 (0)
:os_version_operand_11 ("==")
)
)
: (ProcessMonitor
:type (plugin)
:parameters (
:MyAntivirus.exe (true)
:ShareMyFiles.exe (false)
:begin_admin (admin)
:send_log (alert)
:mismatchmessage ("Please check that the following processes are running:\n1. MyAntivirus.exe\n2. Please check that the following process is not running\n1. ShareMyFiles.exe")
:end (admin)
)
)
: (groupmonitor
:type (plugin)
:parameters (
:begin_or (or1)
:begin_and (1)
:"builtin\administrator" (false)
:"BUILTIN\Users" (true)
:end (1)
:begin_and (2)
:"builtin\administrator" (true)
:"BUILTIN\Users" (false)
:end (and2)
:end (or1)
:begin_admin (admin)
:send_log (alert)
:mismatchmessage ("You are using SecureClient with a non-authorized user.\nMake sure you are logged on as an authorized user.")
:securely_configured_no_active_user (false)
:end (admin)
)
)
: (HotFixMonitor
:type (plugin)
:parameters (
:147222 (true)
:begin_admin (admin)
:send_log (alert)
:mismatchmessage ("Please install security patch Q147222.")
:end (admin)
)
)
: (AntiVirusMonitor
:type (plugin)
:parameters (
:type ("Norton")
:Signature (">=20020819")
:begin_admin (admin)
:send_log (alert)
:mismatchmessage ("Please update your AntiVirus (use the LiveUpdate option).")
:end (admin)
)
)
: (HWMonitor
:type (plugin)
:parameters (
:cputype ("GenuineIntel")
:cpumodel ("9")
:cpufamily ("6")
:begin_admin (admin)
:send_log (alert)
:mismatchmessage ("Your machine must have an\nIntel(R) Centrino(TM) processor installed.")
:end (admin)
)
)
: (ScriptRun
:type (plugin)
:parameters (
:exe ("VerifyScript.bat")
:begin_admin (admin)
:send_log (alert)
:mismatchmessage ("Verification script has determined that your configuration does not meet policy requirements.")
:end (admin)
)
)
: (RegMonitor
:type (plugin)
:parameters (
:string ("SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Domain=testdomain.com")
:begin_admin (admin)
:send_log (alert)
:mismatchmessage ("Your computer doesn't meet the domain membership requirements.")
:end (admin)
)
)
: (SCVMonitor
:type (plugin)
:parameters (
:scv_version ("54014")
:begin_admin (admin)
:send_log (alert)
:mismatchmessage ("Please upgrade your Secure Configuration Verification products package.")
:end (admin)
)
)
: (sc_ver_scv
:type (plugin)
:parameters (
:Default_SecureClientBuildNumber (52032)
:Default_EnforceBuildOperand ("==")
:MismatchMessage ("Please upgrade your SecureClient.")
:EnforceBuild_9X_Operand (">=")
:SecureClient_9X_BuildNumber (52030)
:EnforceBuild_NT_Operand ("==")
:SecureClient_NT_BuildNumber (52032)
:EnforceBuild_2K_Operand (">=")
:SecureClient_2K_BuildNumber (52032)
:EnforceBuild_XP_Operand (">=")
:SecureClient_XP_BuildNumber (52032)
)
)
)
:SCVPolicy (
: (OsMonitor)
: (ProcessMonitor)
: (RegMonitor)
)
:SCVGlobalParams (
:enable_status_notifications (false)
:status_notifications_timeout (10)
:disconnect_when_not_verified (true)
:block_connections_on_unverified (true)
:scv_policy_timeout_hours (168)
:enforce_ip_forwarding (false)
:not_verified_script ("")
:not_verified_script_run_show (false)
:not_verified_script_run_admin (false)
:not_verified_script_run_always (false)
:allow_non_scv_clients (false)
:skip_firewall_enforcement_check (true)
)
)
After the changes to the configuration file local.scv on the SMS install the Policy on the Gateway
5. Test Compliance Checks on the Client
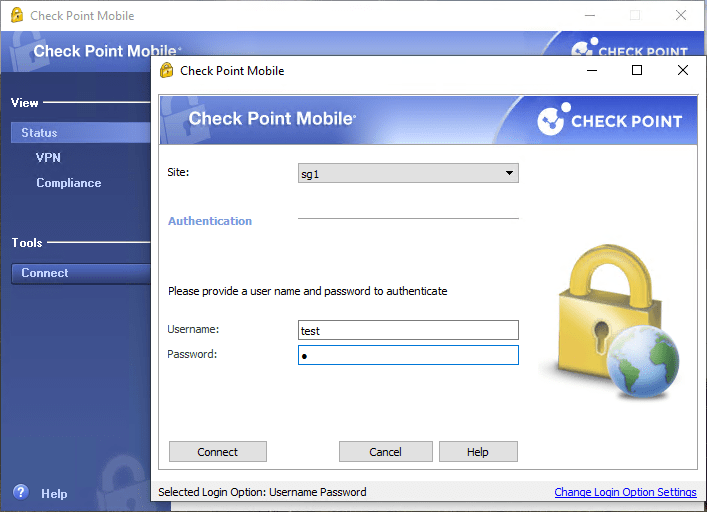
5.1 Check Point Mobile / Connect / Choose Site, Enter Username and Password
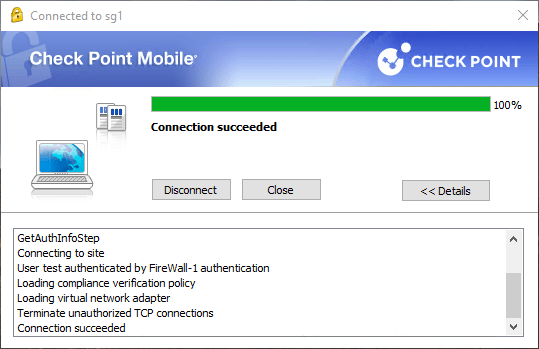
5.2 Connection suceed – Loading compliance verification policy
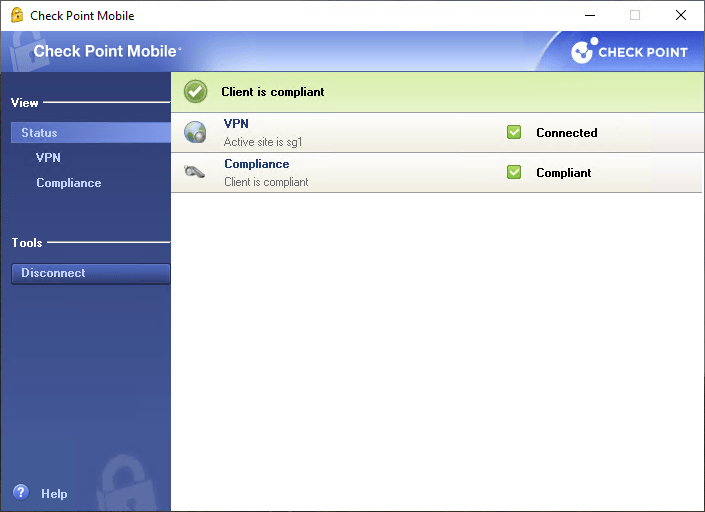
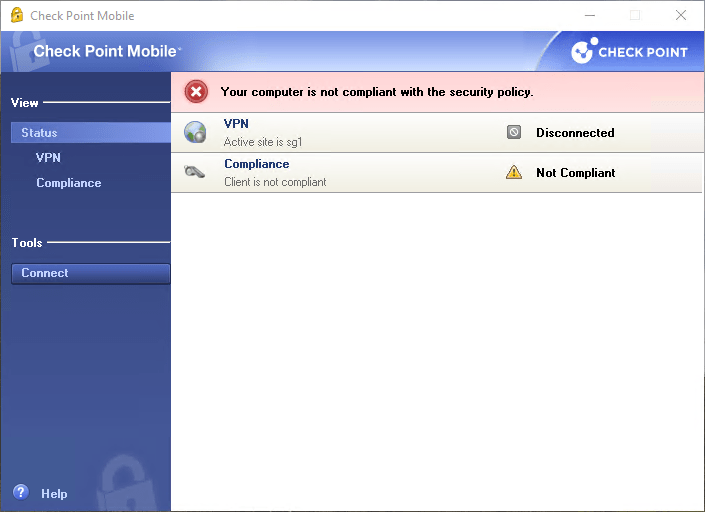
5.3 Compliance Status – Compliant
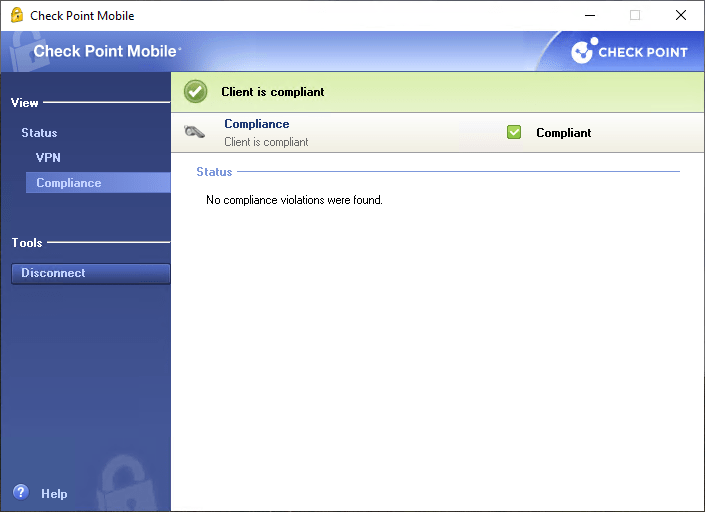
5.4 Compliance Tab – No compliance violations found
5.5 Disconnect the Check Point Mobile from VPN
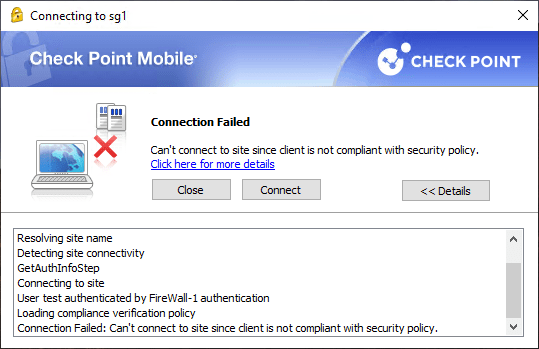
5.6 Now I will terminate the Process MyAntivirus.exe on the Client machine and try to connect again
5.7 Check Point Mobile – Connect
6. Conclusion
This test has shown that if at least one of the configured conditions is not met, the compliance test is not successful. The Client is not conform with company predefined policy.
The compliance tests were successful and demonstrated both states for compliance – compliant / non-compliant.
Check Point Mobile for Windows is now configured and fully functional with Secure Client Verification / Compliance Checks.