There are two most common options how Check Point Security Gateways can be configured as ClusterXL members:
- installing Security Gateways from the beginning as part of the ClusterXL and creating Cluster Object with those new Gateways (in first time wizard – Clustering – unit is part of the cluster, type: ClusterXL)
- creating Cluster Object with existing Security Gateway and adding new Security Gateway to the Cluster
In this Tutorial will be installed ClusterXL with two Security Gateways in High-Availability mode according to the option 2 – with one existing and one new Security Gateway. The first gateway “sg1” is the existing gateway and second gateway “sg2” is the new one. This process is commonly used if there is already one Security Gateway in production environment and the second Security Gateway must be added because of the high-availability or load-balancing needs into the cluster without changing network Gateway IP configuration on all devices in the network. IP Address of the existing gateway sg1 will be used as a cluster IP, so there will not be any changes on the network devices needed.
Both Security Gateways must have the same hardware specification.
CheckPoint – ClusterXL Requirements and Compatibility
Before the start of the configuration it is recommended to create snapshots of the Security Gateway and Security Management Server.
Prerequisites:
- running Security Management Server
- running Checkpoint Security Gateway already connected with Security Management Server
- new Checkpoint Security Gateway
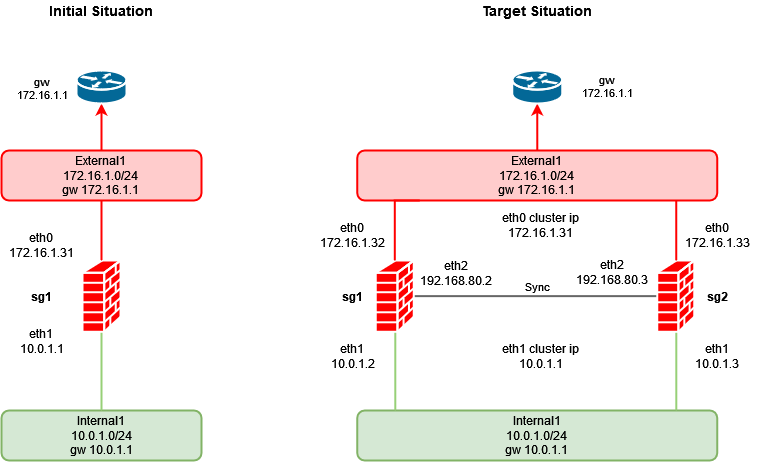
1. Initial and Target Situation
2. Change interface IPs on the existing Security Gateway sg1
3. Sync interface network configuration on existing Security Gateway sg1
4. Enable Cluster membership on sg1
5. Create cluster
6. Cluster network configuration
7. Add second Security Gateway sg2 as member into the cluster
1. Initial and Target Situation
Initial Situation:
Checkpoint SG:
External Interface:
Default gateway:
Internal Interface:
sg1
eth0 172.16.1.31/24
172.16.1.1
eth1 10.0.1.1/24
Target Situation:
Checkpoint SG:
External Interface:
Default gateway:
Internal Interface:
Sync Interface:
cluster1
eth0 172.16.1.31/24
eth1 10.0.1.1/24
sg1
eth0 172.16.1.32/24
172.16.1.1
eth1 10.0.1.2/24
eth2 192.168.80.2/29
sg2
eth0 172.16.1.33/24
172.16.1.1
eth1 10.0.1.3/24
eth2 192.168.80.3/29
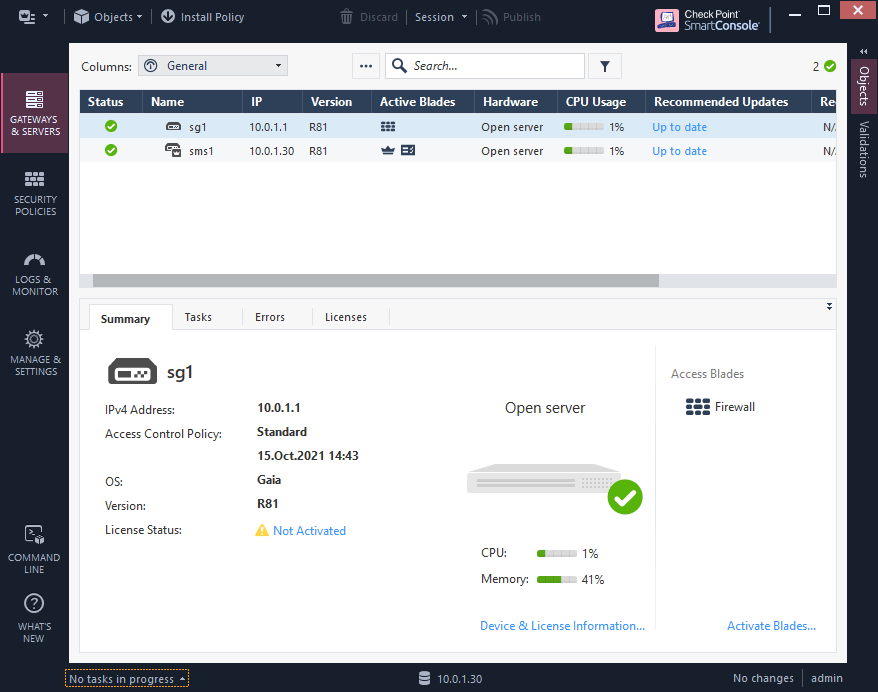
2. Change interface IPs on the existing Security Gateway sg1
2.1 Delete Security Gateway object from SMS
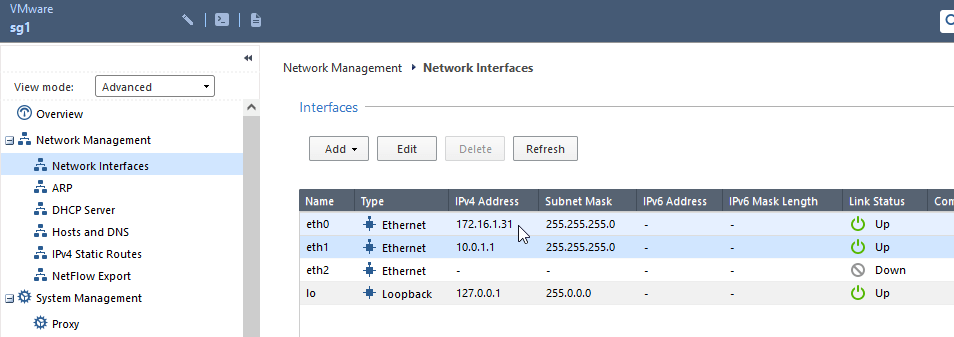
2.2 change interfaces IPs on the Security Gateway. (the old interface IPs will be used for cluster VIP)
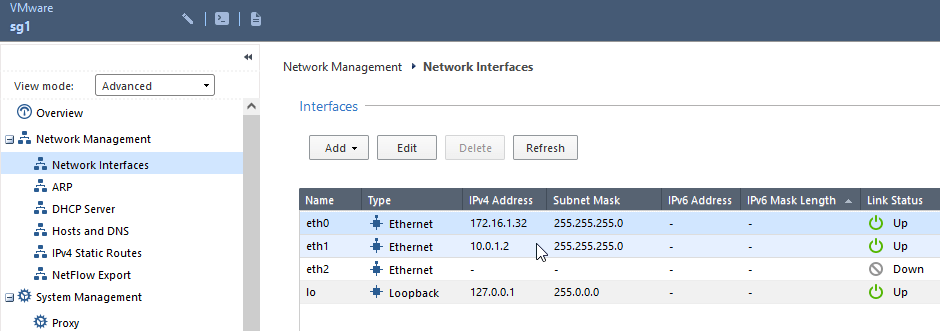
2.3 Reset SIC on Security Gateway sg1
sg1> cpconfig
This program will let you re-configure
your Check Point products configuration.
Configuration Options:
----------------------
(1) Licenses and contracts
(2) SNMP Extension
(3) PKCS#11 Token
(4) Random Pool
(5) Secure Internal Communication
(6) Enable cluster membership for this gateway
(7) Check Point CoreXL
(8) Automatic start of Check Point Products
(9) Exit
Enter your choice (1-9) :5
Configuring Secure Internal Communication...
============================================
The Secure Internal Communication is used for authentication between
Check Point components
Trust State: Trust established
Would you like re-initialize communication? (y/n) [n] ? y
Note: The Secure Internal Communication will be reset now,
and all Check Point Services will be stopped (cpstop).
No communication will be possible until you reset and
re-initialize the communication properly!
Are you sure? (y/n) [n] ? y
Enter Activation Key:
Retype Activation Key:
initial_module:
Compiled OK.
initial_module:
Compiled OK.
Hardening OS Security: Initial policy will be applied
until the first policy is installed
The Secure Internal Communication was successfully initialized
Configuration Options:
----------------------
(1) Licenses and contracts
(2) SNMP Extension
(3) PKCS#11 Token
(4) Random Pool
(5) Secure Internal Communication
(6) Enable cluster membership for this gateway
(7) Check Point CoreXL
(8) Automatic start of Check Point Products
(9) Exit
Enter your choice (1-9) :9
Thank You...
2.4 Connect Security Gateway sg1 with Security Management Server sms1
Check Point Security Gateway R81 Install – How to Tutorial – Step 4
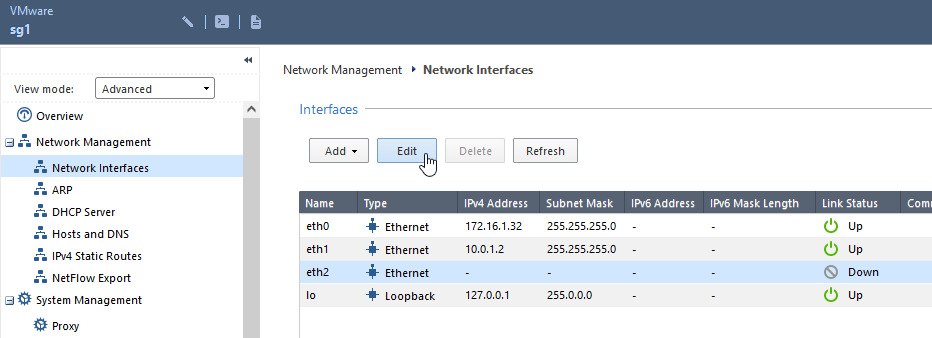
3. Sync interface network configuration on existing Security Gateway sg1
3.1 The simplest way is to use the same interface for internal traffic and cluster Sync at the same time. According to our Architecture Diagram we will use one dedicated network interface per Security Gateway for the ClusterXL synchronization between both cluster members. This is also recommended best practice from Check Point.
On the existing Security Gateway sg1 will be used eth2 interface as cluster Sync interface. This interface must be enabled and fitted with IP configuration before cluster configuration, so we can use this interface in our topology configuration in cluster object later. For dummy IP address will be used range 192.168.80.0/29 which should not be used anywhere in the network and on the existing Security Gateway as well.
Sync Interface best practises:
Sync interface IP assignment best practice
Best Practice for HA Sync interface
Note:
I recommend to use larger sync network range e.g. /29 (6 usable IPs) in comparison to /30 range (2 usable IPs which would be sufficient in use case with 2 cluster members) in case you will have to add new cluster member. For most cluster setups with max 6 cluster members in production it will be sufficient.
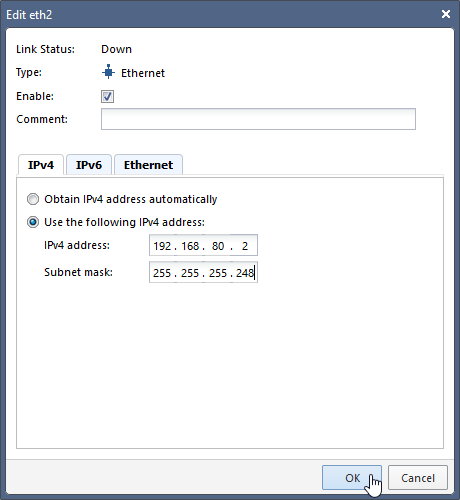
3.2 Configure eth2 sync interface on Security Gateway sg1 according to Network Diagram in Chapter 1 with IP 192.168.80.2/255.255.255.248 and enable the interface.
4. Enable Cluster membership on sg1
4.1 run cpconfig tool on the sg1 and select “6” for “Enable cluster membership for this gateway”, acknowledge with “y”. Reboot the machine: “reboot”, acknowledge with “y”.
sg1> cpconfig
This program will let you re-configure
your Check Point products configuration.
Configuration Options:
----------------------
(1) Licenses and contracts
(2) SNMP Extension
(3) PKCS#11 Token
(4) Random Pool
(5) Secure Internal Communication
(6) Enable cluster membership for this gateway
(7) Check Point CoreXL
(8) Automatic start of Check Point Products
(9) Exit
Enter your choice (1-9) :6
Enable cluster membership for this gateway...
==============================================
You have selected to enable cluster membership for this Security Gateway.
Are you sure? (y/n) [y] ? y
Cluster membership for this gateway was enabled successfully
Important: This change will take effect after reboot.
sg1> reboot
Are you sure you want to reboot?(Y/N)[N]
y
sg1>
5. Create cluster
5.1 new Cluster – Cluster – Classic Mode.
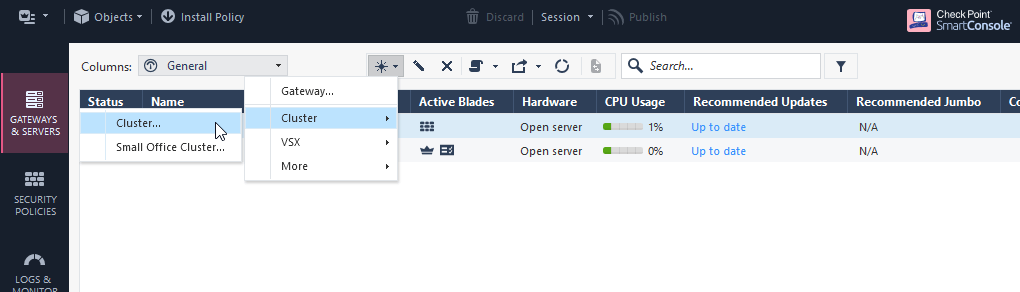
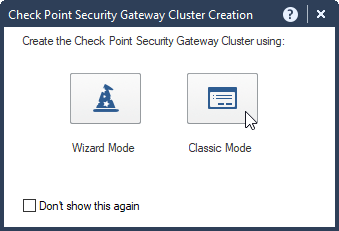
5.2 Type in Cluster name “cluster1” and main IP Address of the cluster “10.0.1.1”.
Note:
In most cases the main cluster IP address is the VIP address of the internal or DMZ interface which resides in the same subnet as the Security Management Server. In cases of routed networks between Security Gateway and Security Management Server choose interface with shortest path between SG and SMS.
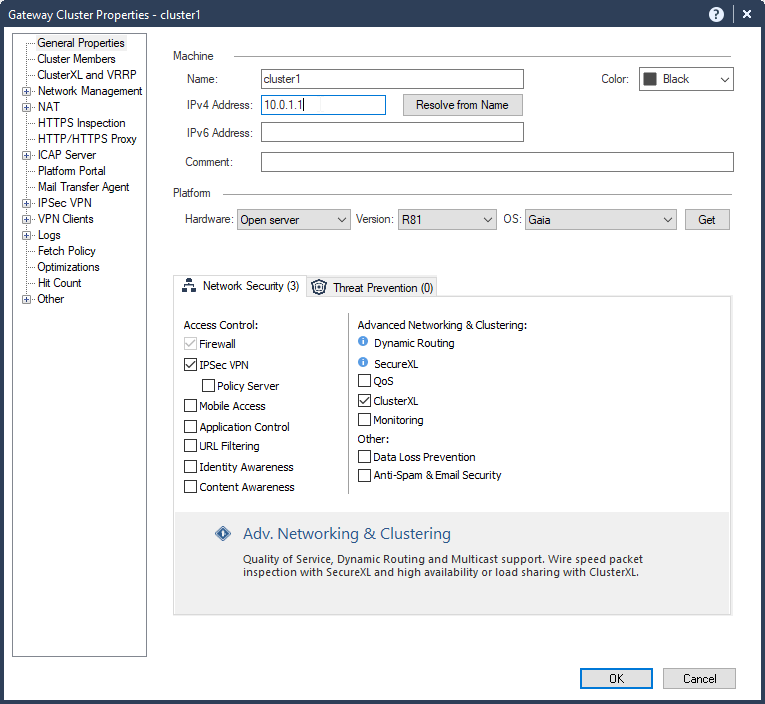
5.3 Uncheck “IPSec VPN” blade unless you need the VPN blade.
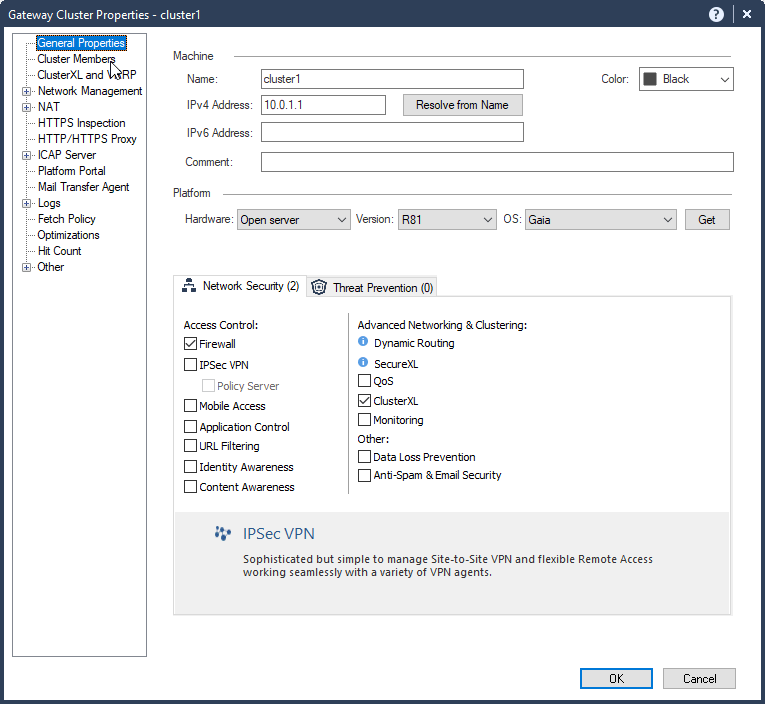
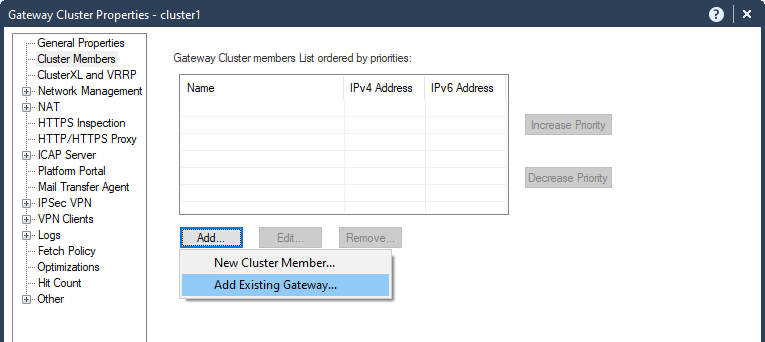
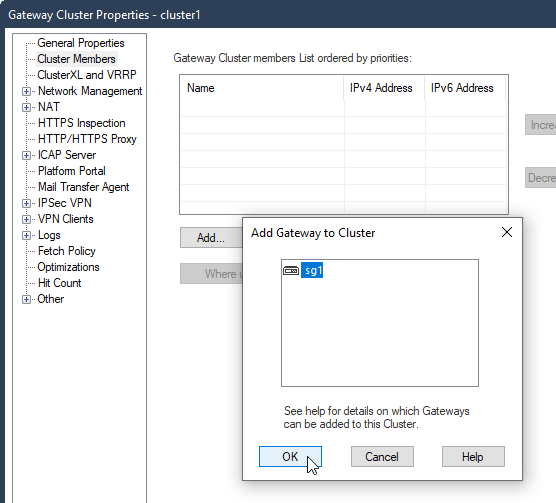
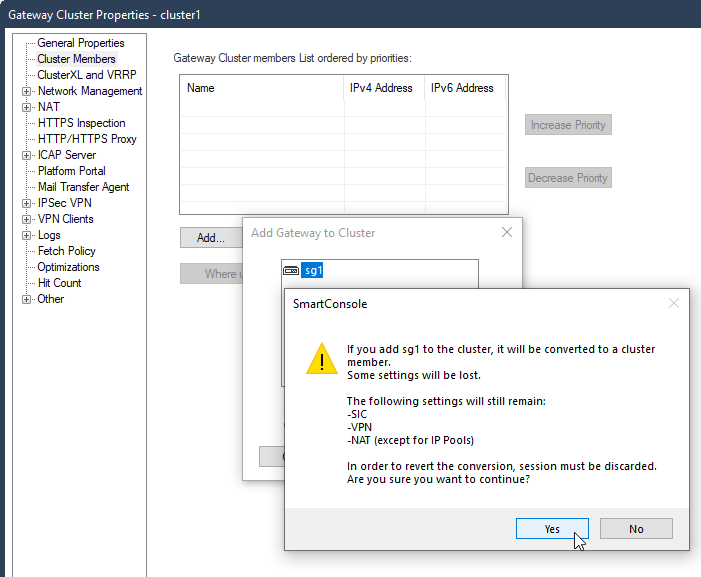
5.4 Cluster Members – Add – Add Existing Gateway – sg1 – Yes – Ok
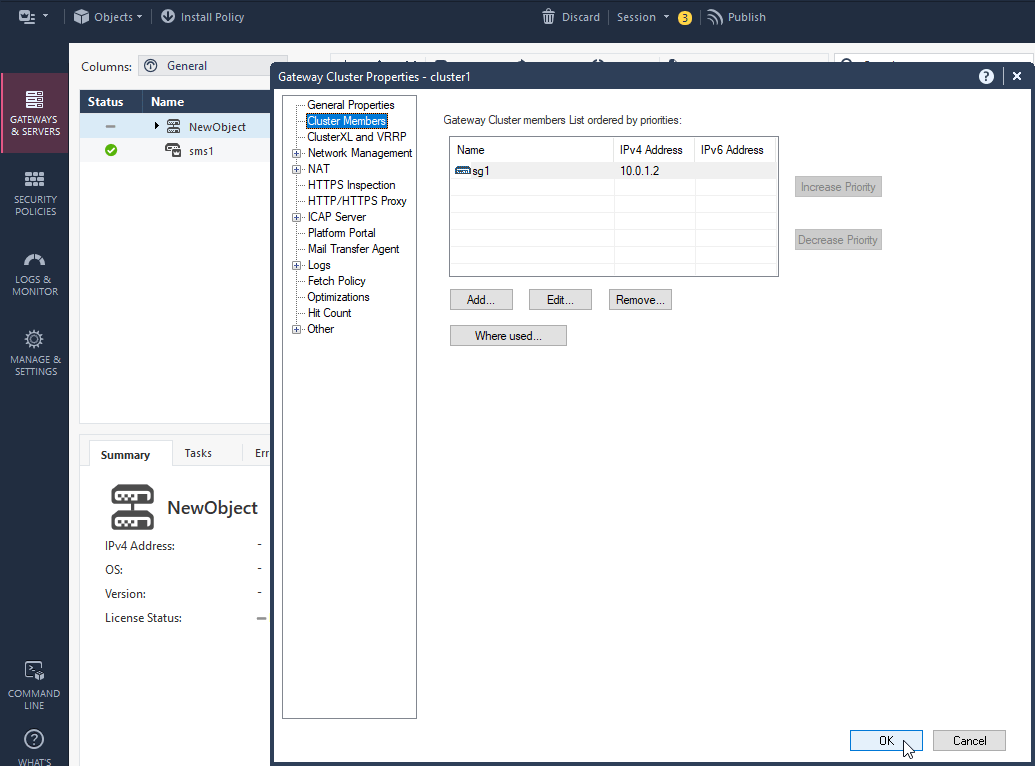
6. Cluster network configuration
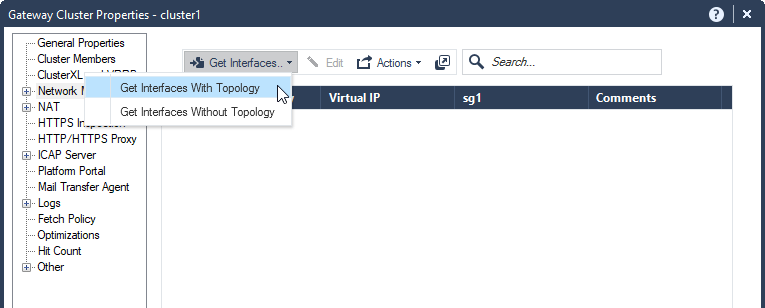
6.1 Network Management – Get Interfaces – Get Interfaces With Topology – Yes
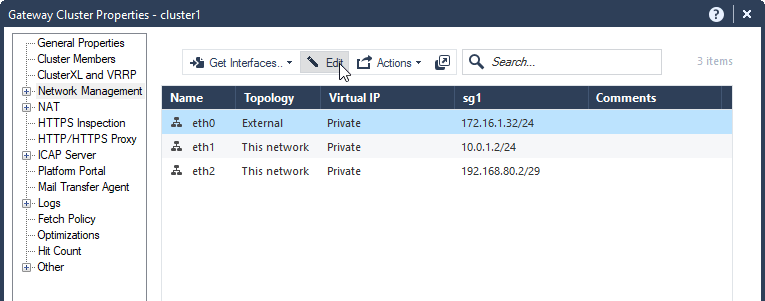
6.2 Configure VIP for each cluster interface. Select Network Type: cluster, For eth0 172.16.1.31/24, eth1 10.0.1.1/24.
Note:
Check interface configuration and make corrections to “Leads To”, “Security Zone”, “Anti Spoofing” according to your needs.
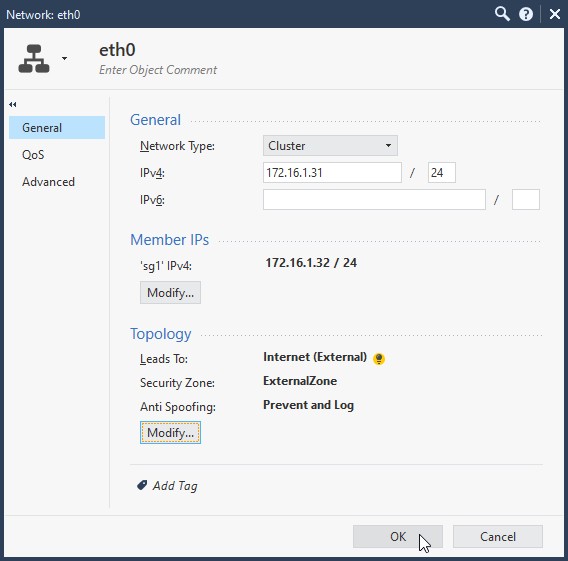
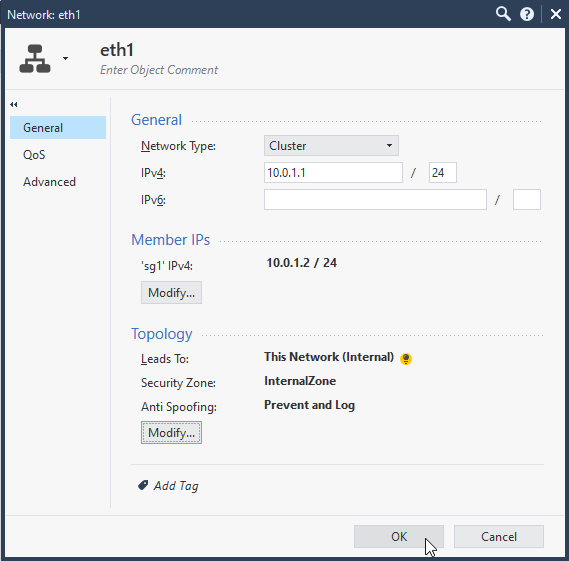
6.3 Configure Sync cluster interface (or more). Select Network Type: Sync, For eth2 192.168.80.2/29.
Note:
Check interface configuration and make corrections to “Leads To”, “Security Zone”, “Anti Spoofing” according to your needs.
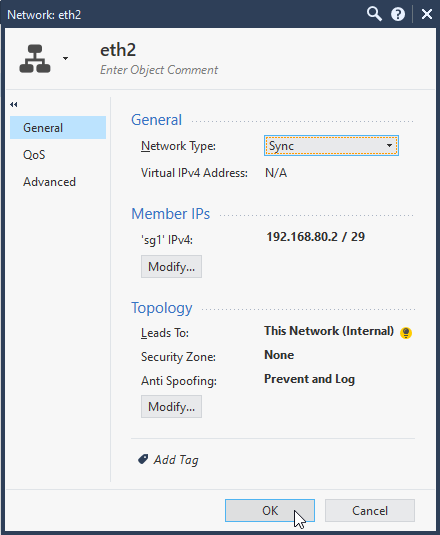
6.4 VIPs and cluster Sync configuration for the new cluster is done. Select OK.
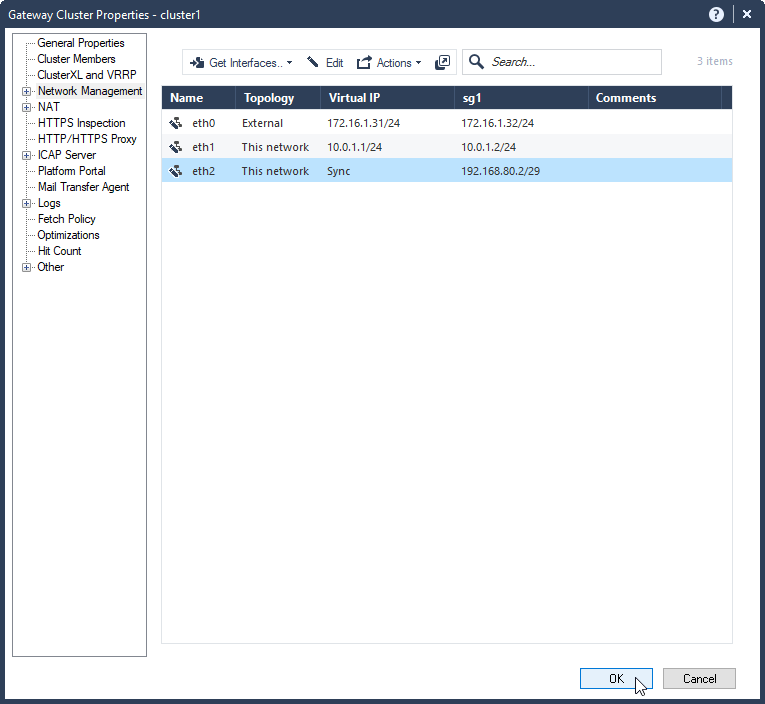
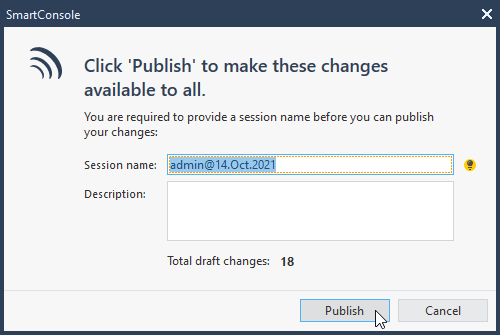
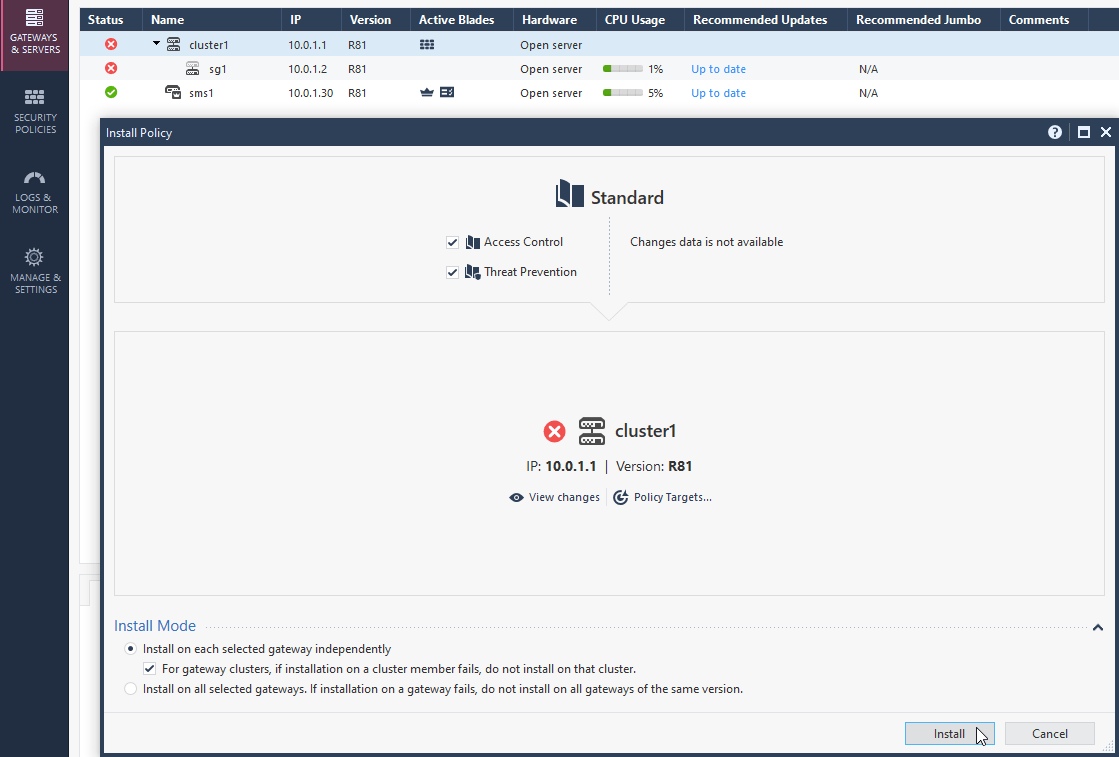
6.5 publish changes and install policy.
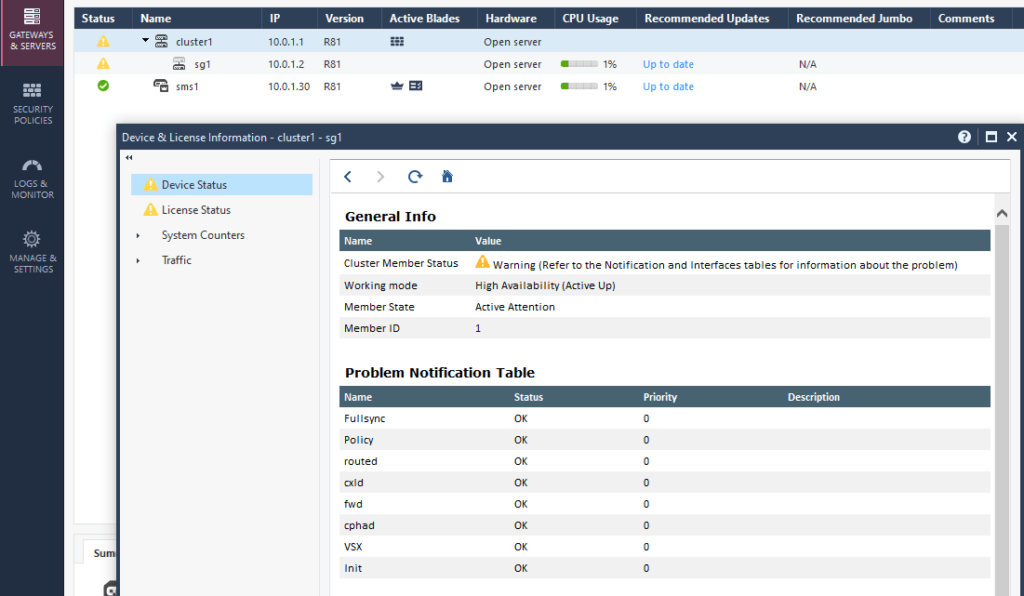
sg1> show cluster state Cluster Mode: High Availability (Active Up) with IGMP Membership ID Unique Address Assigned Load State Name 1 (local) 192.168.80.2 100% ACTIVE(!) sg1 Active PNOTEs: IAC Last member state change event: Event Code: CLUS-116505 State change: INIT -> ACTIVE(!) Reason for state change: All other machines are dead (timeout), Incorrect configuration - Sync interface has not been detected Event time: Thu Oct 14 17:05:26 2021 Cluster failover count: Failover counter: 0 Time of counter reset: Thu Oct 14 16:24:07 2021 (reboot) sg1>
6.6 After brief moment (cca 1-2 min) the new Checkpoint Firewall Cluster “cluster1” is functional with one Security Gateway “sg1”. The new Cluster “cluster1” is now processing network traffic according to the existing policy “standard” which was used on the Security Gateway before migrating to cluster member. Security policy should be checked and possibly adjusted by reason of the sg1 IPs change.
7. Add second Security Gateway sg2 as member into the cluster
7.1 open cluster object “cluster1” – Cluster Members – Add – New Cluster Member
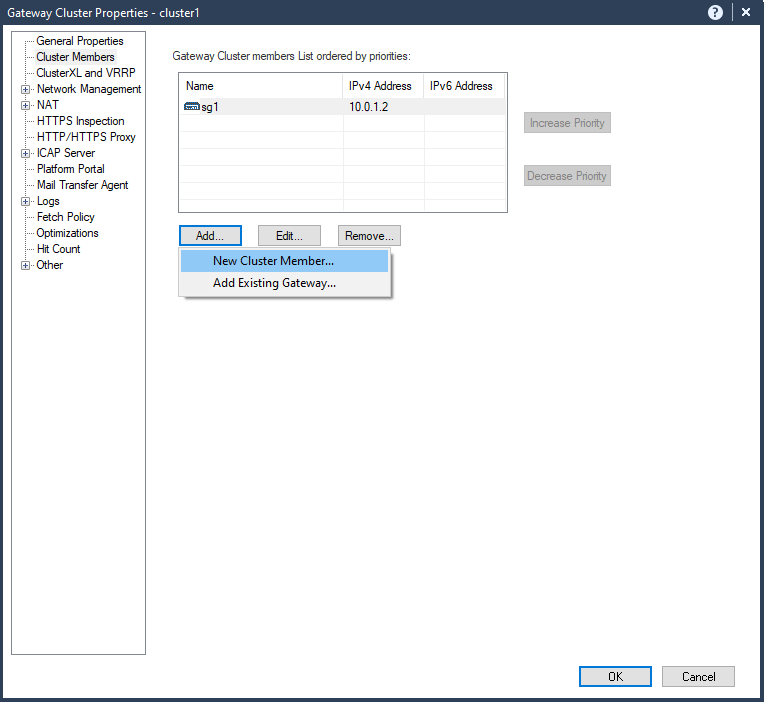
7.2 Type in name of the second Security Gateway (usually hostname typed during installation) “sg2” and management IP address (configured during installation), Select “Communication”.
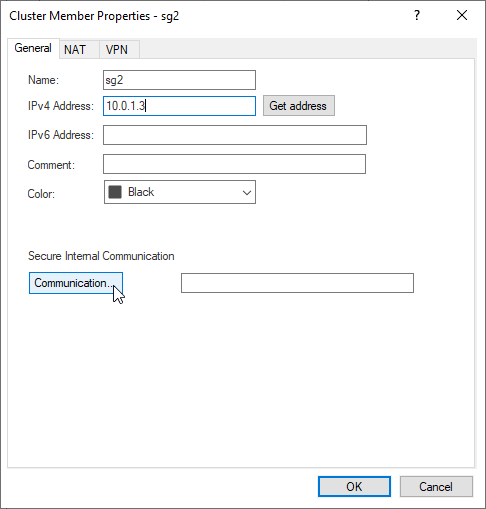
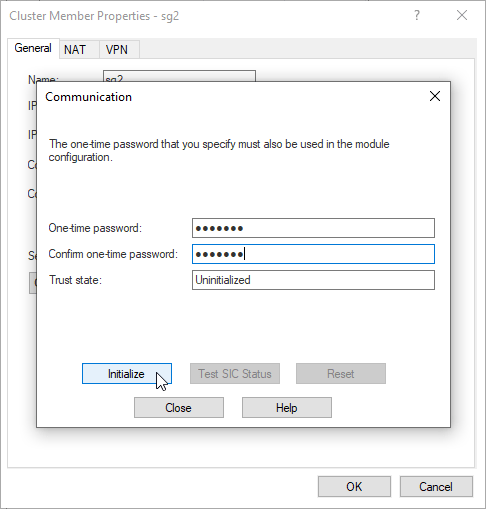
7.3 Type in activation key – one time password configured during sg2 installation. Click Initialize.
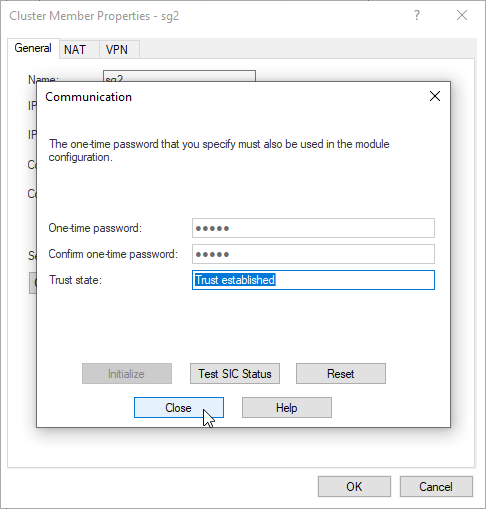
7.4 Trust between Security Gateway and Security Management Server is established. Click Close. Click Ok
Note:
more about Secure Internal Communication (SIC)
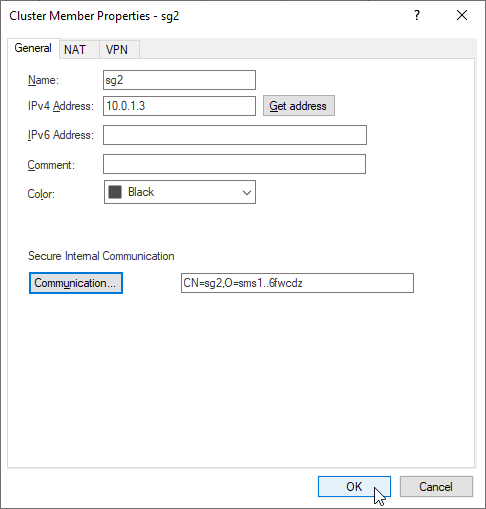
7.5 Configure interface IPs for the second Security Gateway sg2:
eth0 172.16.1.33/24
eth1 10.0.1.3/24
eth2 192.168.80.3/29
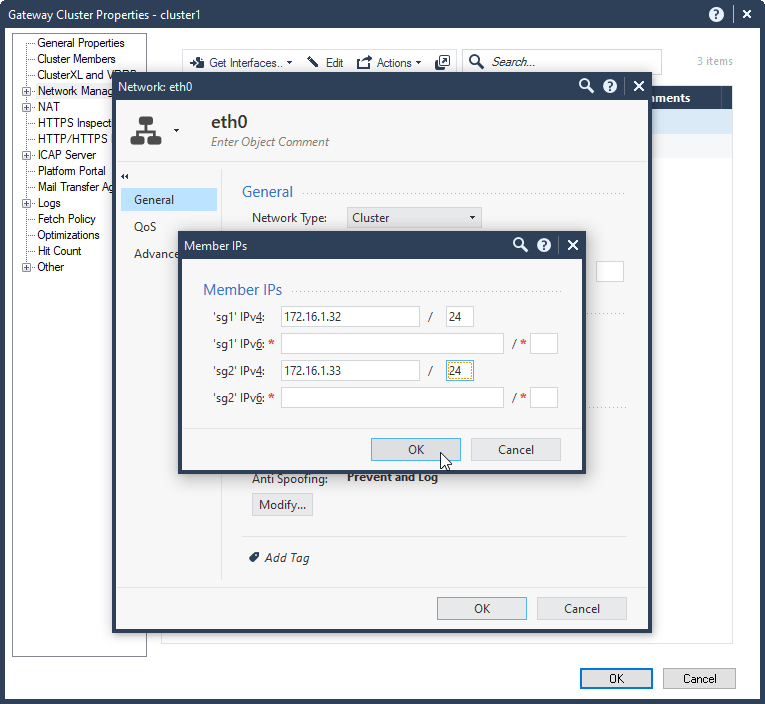
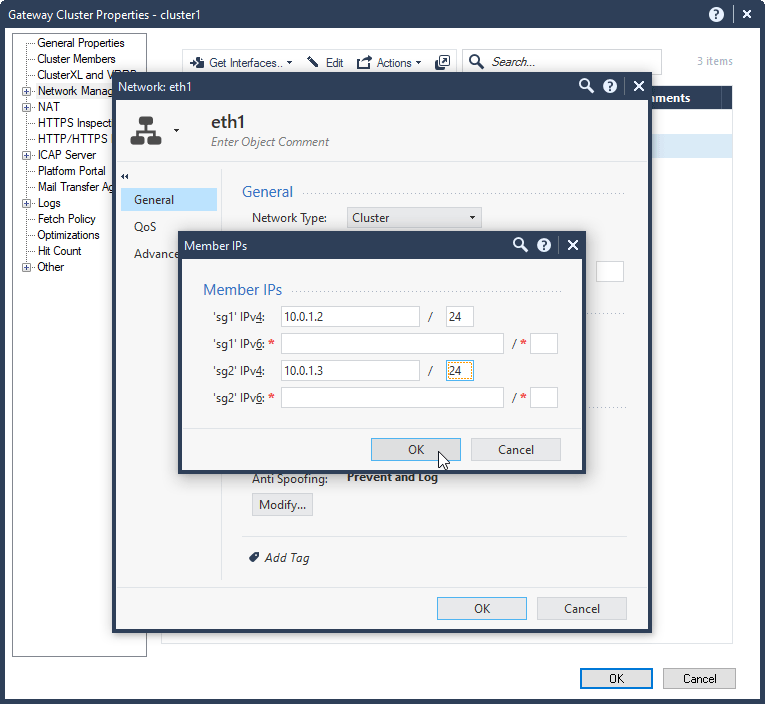
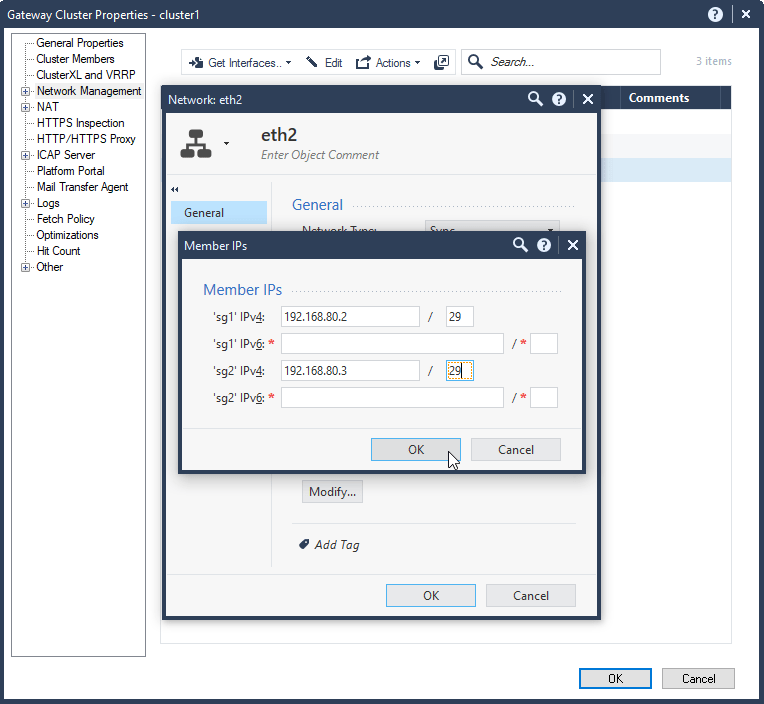
7.6 Check network configuration. Select Ok.
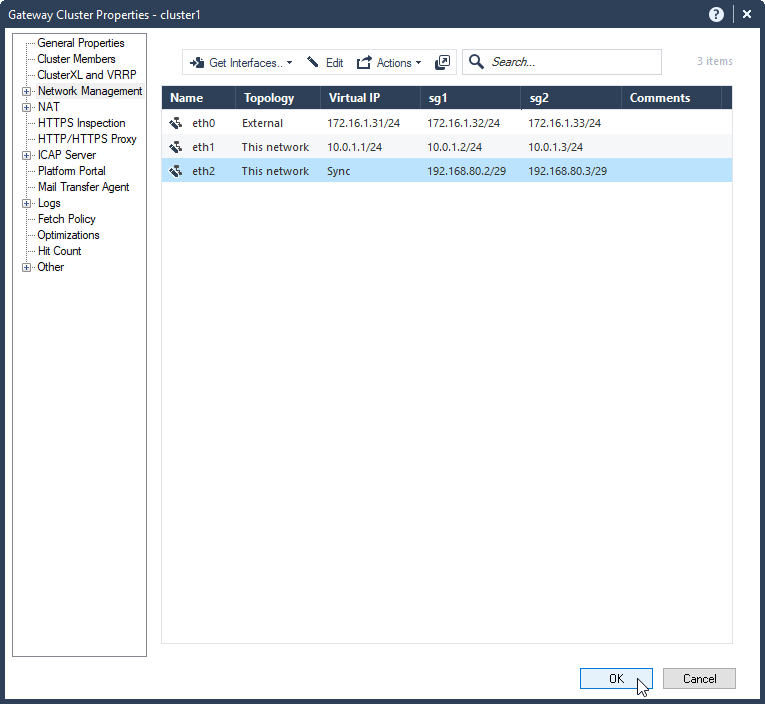
7.7 publish and install changes.
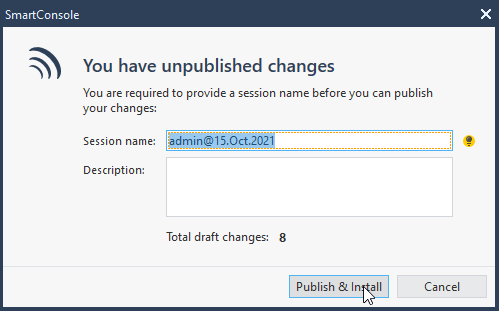
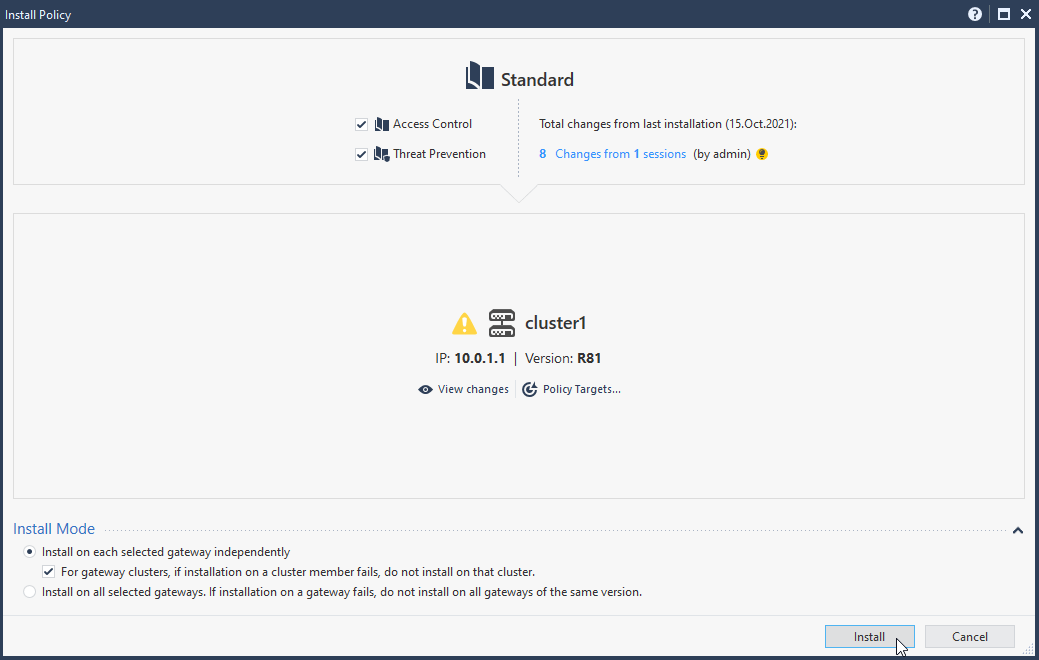
7.8 after couple of moments (1-2 min) alls statuses should be in green.
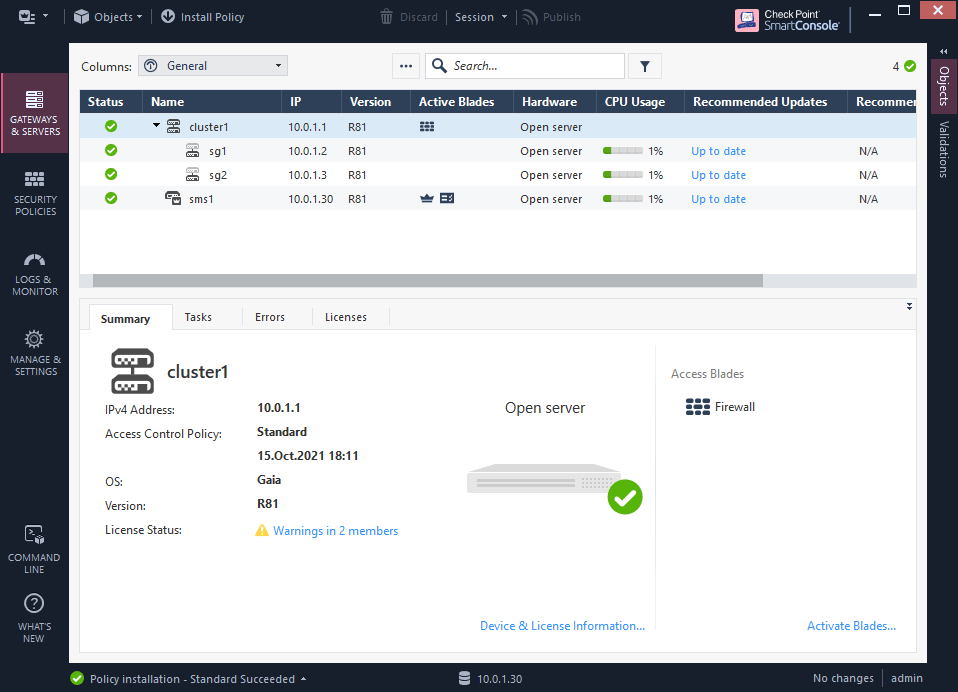
7.9 quick check of the cluster status and health.
Note:
If there are none PNOTEs present the cluster is healthy.
sg1> show cluster state Cluster Mode: High Availability (Active Up) with IGMP Membership ID Unique Address Assigned Load State Name 1 (local) 192.168.80.2 100% ACTIVE sg1 2 192.168.80.3 0% STANDBY sg2 Active PNOTEs: None Last member state change event: Event Code: CLUS-116505 State change: INIT -> ACTIVE(!) Reason for state change: All other machines are dead (timeout), Incorrect configuration - Sync interface has not been detected Event time: Fri Oct 15 18:07:59 2021 Cluster failover count: Failover counter: 0 Time of counter reset: Fri Oct 15 18:04:33 2021 (reboot) sg1>
The new cluster “cluster1” is now configured and fully functional.